
E-voting in Web3
Cybersecure online voting can be achieved by making a correct use of cryptography, eID & blockchain.Voting in the online context simply means voters are the auditors:YOU vote, verify & validate
(also known as end-to-end verifiability)
STRONG IDENTITY MANAGEMENT
Sybil resistant
Each vote should count at most once during each polling. To achieve this, strong IDM is required. We use eID embedded in national ID smart cards.


Zero knowledge Proofs
Homomorphic encryption
Public-key cryptography
Cryptography
The vote must be private and verifiable. While these two proprieties may seem contradictory, with smart mathematics we can design an E2E verifiable tokenized system.
Extra security
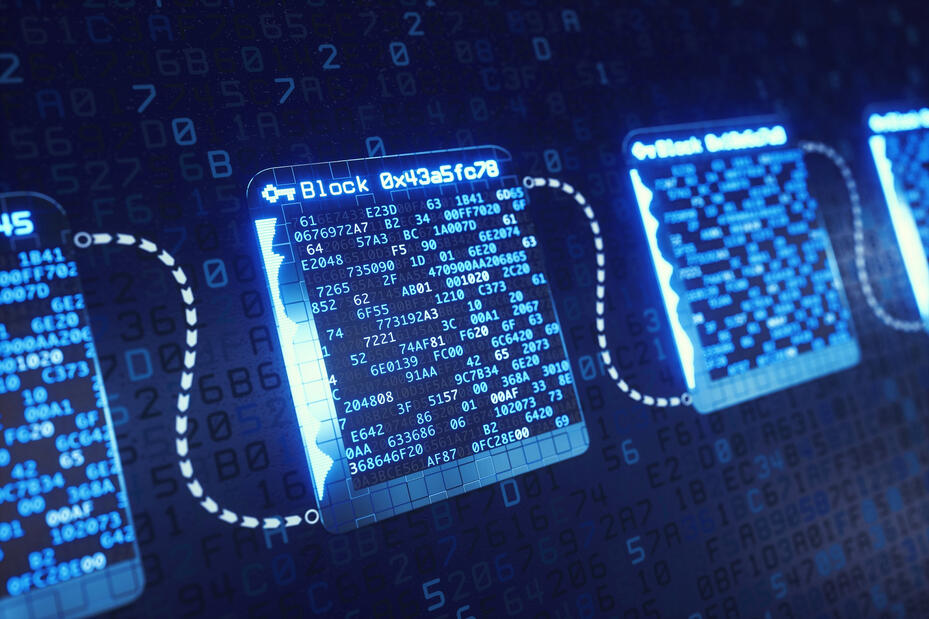
Blockchain
Cybersecurity is primodial.By decentralizing the digital ballots we prevent double voting and modification of previous records.
Digital politics
Decentralize political decisions
"The political discourse has shifted from traditional media outlets (TV, radio, newspapers) to the internet as fast as the tech matured. As we move on from the Web 2.0 architecture to the new Web3 frontier, one goal should remain clear: the platforms of the future are to be cybersecure, be respectful of privacy and to be censorship resistant."

Contacts
Get to know us!
We are at pre-seed stage with an alpha product in hands. Feel free to contact us if you are interested.